How To: Make Ubuntu Show Asterisks When Typing Password
shoulder-surfing won’t be able to see the number of characters in your password. This is how to get some feedback when you enter your password in the terminal.
[code]sudo nano /etc/sudoers[/code]
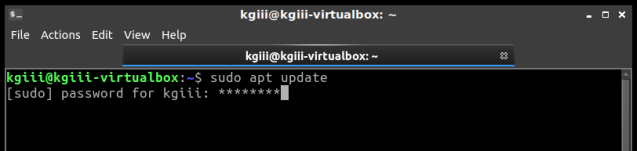
Enter your password and hit enter, of course. (This will be the last time you enter your password in the terminal without some sort of visual feedback!)
Now it gets a little tricky.
Use the down arrow until your at the start of the line that says:
[code]Defaults mail_badpass[/code]
Press the ENTER button. This should move that line down and leave a blank line above it. Use the arrow button to move up to that blank line and enter:
[code]Defaults[/code]
Then press the TAB button on your keyboard. This will move the cursor to the right location. Add this text:
[code]pwfeedback[/code]
The entire line should look something like:
[code]Defaults pwfeedback[/code]
Press CTRL + X, then Y, and then ENTER.
[code]sudo apt update[/code]
Original advisory details: It was discovered that wpa_supplicant did not properly handle P2PUSN-4757-2: wpa_supplicant and hostapd vulnerability
provides the corresponding update for Ubuntu 14.04 ESM.
(Wi-Fi Direct) provision discovery requests in some situations. A
physically proximate attacker could use this to cause a denial of service
or possibly execute arbitrary code.
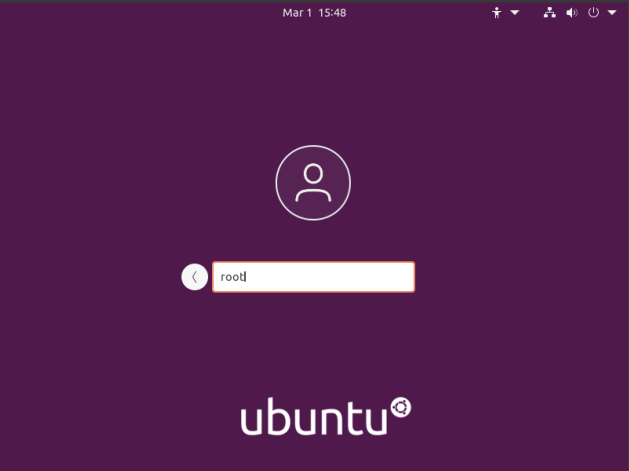
How To: GUI Login as Root in Ubuntu
The first step is to set up the system so that you can login as root. To do that, you have to enable root login for Ubuntu. You should probably read the warnings on that page and you should think carefully before doing this to your own computer.
The next step is to crack open your default terminal emulator. You can do that by pressing CTRL + ALT + T.
[code]sudo su[/code]
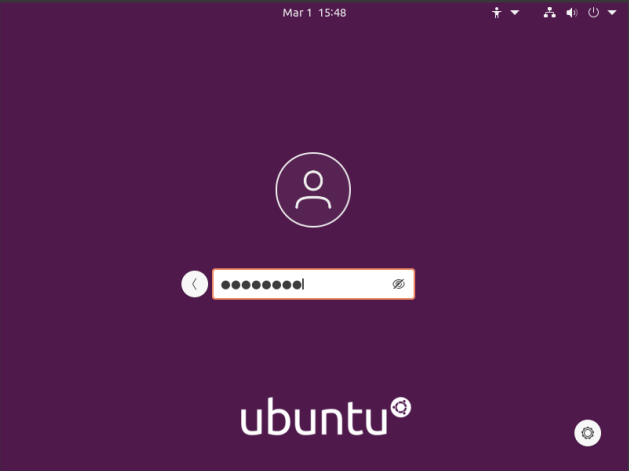
(Press enter and enter your password, of course.)
Our next step is to tell GDM3 to let us use the root login.
[code]nano /etc/gdm3/custom.conf[/code]
[code]AllowRoot=true[/code]
[code]nano /etc/pam.d/gdm-password[/code]
Now, scroll down and look for this line:
[code]auth required pam_succeed_if.so user != root quiet_success[/code]
So, change that line so that it looks like this:
[code]#auth required pam_succeed_if.so user != root quiet_success[/code]
Now, save it just like you did above. (Press CTRL + X, then Y, and then ENTER.)
[code]exit[/code]

USN-4757-1: wpa_supplicant and hostapd vulnerability
(Wi-Fi Direct) provision discovery requests in some situations. A
physically proximate attacker could use this to cause a denial of service
or possibly execute arbitrary code.
USN-4754-4: Python 2.7 vulnerability
subsequent update removed the fix for CVE-2021-3177. This update reinstates
the security fix for CVE-2021-3177.
We apologize for the inconvenience.
Original advisory details:
It was discovered that Python incorrectly handled certain inputs.
An attacker could possibly use this issue to execute arbitrary code
or cause a denial of service. (CVE-2020-27619, CVE-2021-3177)