shoulder-surfing won’t be able to see the number of characters in your password. This is how to get some feedback when you enter your password in the terminal.
[code]sudo nano /etc/sudoers[/code]
Enter your password and hit enter, of course. (This will be the last time you enter your password in the terminal without some sort of visual feedback!)
Now it gets a little tricky.
Use the down arrow until your at the start of the line that says:
[code]Defaults mail_badpass[/code]
Press the ENTER button. This should move that line down and leave a blank line above it. Use the arrow button to move up to that blank line and enter:
[code]Defaults[/code]
Then press the TAB button on your keyboard. This will move the cursor to the right location. Add this text:
[code]pwfeedback[/code]
The entire line should look something like:
[code]Defaults pwfeedback[/code]
Press CTRL + X, then Y, and then ENTER.
[code]sudo apt update[/code]
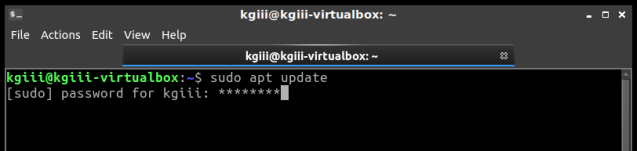 See? Asterisks for feedback in the terminal.
See? Asterisks for feedback in the terminal.
USN-4757-1 fixed a vulnerability in wpa_supplicant and hostapd. This update
provides the corresponding update for Ubuntu 14.04 ESM.
Original advisory details:
It was discovered that wpa_supplicant did not properly handle P2P
(Wi-Fi Direct) provision discovery requests in some situations. A
physically proximate attacker could use this to cause a denial of service
or possibly execute arbitrary code.
